ON PREM VS. SASE: WHICH FIREWALL IS RIGHT FOR YOUR BUSINESS?
Three things in life are certain: death, taxes and the persistent threat of cyberattacks. There are many layers of defense in the onion of cyber security, but at the helm is your firewall. Traditionally firewalls have always been the piece of hardware acting as a barrier between your office network and the wilds of the internet. Then in 2020 the way we work was transformed forever by the global pandemic. Nearly a third of the workforce transitioned to remote, leaving offices empty. Many employees continue to work in non-traditional spaces to this day. How can we defend them against cyberattacks if they are outside the protective reach of an on premise firewall?
A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Think of it as a moat with a bridge and a guard shack that surrounds a castle. The guards and the moat are the firewall, acting as a barrier and between a trusted internal network (the castle) and untrusted external networks (random people trying to get in), helping to prevent unauthorized access to and from the castle while allowing legitimate traffic to pass through. The outside forces have to “check in” with the guards before they can cross the moat and access the castle.
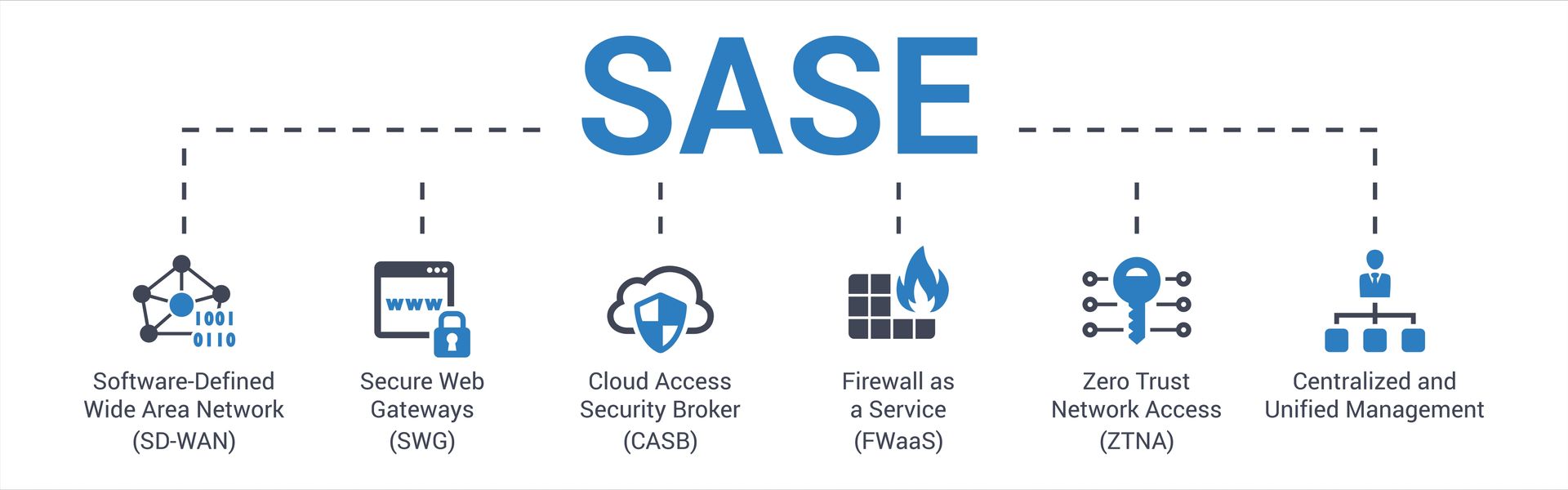
With SASE, short for Secure Access Service Edge, the moat and guards become portable. When using SASE, pronounced "sassy," this software is installed directly on devices to monitor network traffic no matter your location. It functions as a unified security system and network connection, safeguarding users and data while ensuring speedy and dependable access to the internet and cloud-based applications from any location. Just like an on prem firewall it is managed remotely by your admin team.
For most companies, a hybrid solution may be the best option. For example a company may have a central office in Boston with 30 users, but also 3 sales people who travel frequently and need protection. Both SASE and a traditional firewall would be necessary to protect everyone.
Overall, firewalls play a crucial role in enforcing network security policies, controlling traffic flow, protecting against cyber threats, and safeguarding your network, so you must chose wisely!
Uncomplicate IT News Blog